Saturday, 4 August 2012
Friday, 3 August 2012
Download Top 6 Image Editing Software for Free
you can Download Some best and top 6 Photo Editing Software Torrents
just click on the below link to download and start it with your torrent downloader
http://tiny.cc/8impe <<<( ADOBE PHOTOSHOP ELEMENTS 9 )
http://tiny.cc/sty42 <<<( Corel Paint Shop Pro Photo X3 )
http://tiny.cc/1j468 <<< ( Xara 3D Version 6 )
http://tiny.cc/qw3of <<<( Serif PhotoPlus x2 Studio Pack )
http://tiny.cc/lvya1 <<<( Nikon Capture NX v2.1 )
http://tiny.cc/eey60 <<<( ArcSoft PhotoStudio 6 )
Snow Bros 1 2 3 PC Game Collection Full Version Free Download
The gameplay of Snow Bros is very similar to Bubble Bobble, released in 1986. The game supports up to two players, with each player taking the part of one of two snowmen Nick and Tom. Each player can throw snow at the enemies. The player must throw snow at each enemy until it is completely covered, when it turns into a snowball. An enemy partially covered in snow cannot move until it shakes it off.
Once an enemy has been turned into a snowball the player can roll it. The snowball will re-bound off walls, until eventually shattering against a wall. Any enemies the snowball rolls into are eliminated and other stationary snowballs start rolling when the rolling snowball touches them. If the player manages to take out all of the enemies with kicking one snowball (this one snowball may be used to make others bounce around as well and increase the chances to pull this trick off), money in the form of large green bills will fall from the sky. These disappear in a very short amount of time but are worth 10,000 points each, the most the player can get as a bonus. Every tenth level there is a boss. Each boss can sustain being hit a number of times. In Sega Genesis port, after the 50th level, you play as one of the snow castle princesses. When a player bowls an enemy over, it may drop a lantern. The color of the lantern lets the player know what special power-up he or she will acquire:
- Red increases walking speed.
- Blue increases amount of snow thrown, thus making it easier to cover an enemy in snow.
- Yellow increases the distance that snow can be thrown.
Green causes your character to inflate like a balloon while having the ability to fly around screen and knock out enemies for a limited period of time. The effects of the red, blue, and yellow lanterns wear off after the player loses a life. If the player takes too much time to complete a level an evil pumpkin head will come and try to kill the player character. It is invincible but can be stunned and sent to appear somewhere else in the level with snowballs or snow shots. After a short time the evil pumpkin will spawn ghosts that can travel freely through the level and seek the player character. These ghosts can't be killed or stunned, so the player's only hope is to avoid them while eliminating the rest of the enemies to move on to the next screen as soon as possible.
Metal Slug PC Game Collections Full Version Free Download
The gameplay of the series is characteristic of run and gun games: large numbers of enemies and a player character with extremely powerful weapons. In most run and guns, contact with an enemy leads to annihilation. In this series, however, contact results in the opportunity to perform a melee attack and the opportunity for the enemy to perform a melee attack of his own if he has one. The player's melee attack is also much stronger than most shots. This leads to the ability for the player to run in and use melee attacks to take down a number of troops, and the ability to quickly defeat enemies that can take plenty of damage like the mummies in Metal Slug 2.
The player starts with only a simple pistol, as the game progresses the player picks up new weapons. The player can only carry one weapon at the time, when a new weapon is found it replaces the old one. Similarly, when the ammo runs out, the player reverts to using the handgun. A new system was implemented with Metal Slug 6 allowing players to carry two larger weapons and switch between them as well as the default pistol.
The SV-001 or Metal Slug is the main vehicle of the Metal Slug franchise. It is a small, cartoonish silver-gray tank (SV is short for "Super Vehicle"). The tank is armed with one cannon and twin vulcan cannons. The vehicle can jump and crouch. Crouching opens a hatch on the top of the tank through which grenades can be thrown. The grenades are independent of the cannon's ammo system. The vehicle can run over infantry and perform a suicide attack, with the driver jumping clear and the tank ramming into and exploding upon the target. The vehicle can take three direct hits before it is destroyed. The enemy chaser variant has a shield that must be destroyed before the vehicle can be destroyed. It is propelled by caterpillar treads. Over time, these specifications changed into any vehicle armed with a vulcan cannon and a cannon variant suited to the role of the vehicle, and propelled suitably for that vehicle's environment. In Metal Slug 6 (and the home version of Metal Slug X, 3, 4, 5), Tarma can lock the vulcan cannons into one position and fire continuously. The "slug gunner" is considered the epitome of slug evolution.
Processor= 233MHz
Ulead Media Studio Pro 8 Full Version Free Download
Ulead MediaStudio Pro 8 is powerful, versatile and intuitive video editing software, for professionals and enthusiasts in independent production, event videography, business, and education. Integrated, quick-to-master tools take you to the forefront of professional real-time HDV, DV or MPEG editing.
Openings that Rock
Create professional-quality opening sequences or segues instantly- with pre-made masks, frames and moving paths. Export sequences as virtual clips, which can be opened and further tweaked.
Smart Proxy: Real-time HDV
HDV editing, even on mid-range or mobile machines - in real-time! Completely lossless, your final output always links back to the original full-resolution files. The perfect solution for producers shooting HDV, who want to edit on the go.
Extensive HDV Support
Batch capture HDV from all the latest HDV camcorders and decks. Edit HDV either in full-resolution lossless native format. Record your finished HDV projects back to your camera or output to WMV-HD
1. Install setup EXE.
2. Don't run program.
3. Run the crack to unlock the program.
Ad-Aware Internet Security Pro v10.0.138.2879 + Serial Key
Ad-Aware Internet Security Pro v10.0.138.2879 + Serial Key || File Size : 2.17 MB.
Ad-Aware Internet Security gives you the power to combat identity thieves and cyber threats, including the most complex forms of malware, protecting you from viruses, spyware, trojans, rootkits, keyloggers, password stealers, and much more. With minimal strain on system resources and advanced real-time detection technology, Ad-Aware gives you the ability to use the Internet how, when, and where you want — without the worry.
Features:
* Complete Malware Protection, Including Anti-Virus and Anti-Spyware
* Ad-Watch Live! Expert Real-time Protection
* NEW! Genotype Detection Technology
* NEW! Behavior-Based Heuristics Detection
* NEW! Expert Level Rootkit Removal System
* NEW! The Neutralizer Malware Removal Tool
* NEW! Do Not Disturb Mode
* Minimal Strain on System Resources
* NEW! Download Guard for Internet Explorer
* Toolbox Including Process Watch, AutoStart Manager, Hosts File Editor, and ThreatWork
* Customizable Profile Scans
* Network Drive Scanning
* Automatic Pulse Updates & Free Technical Suppor
Installation
1. Unpack rar archive
2. Run installer Ad-Aware Internet Security Pro v10.0.138.2879.exe
3. Enjoy.
Outertech Cacheman v7.50 + Serial
Outertech Cacheman v7.50 + Serial || File Size : 3.35 MB.
Cacheman is a handy software that helps you speed up your computer.
Have you been wondering how to speed up your computer? Cacheman (short for Cache-manager), the award-winning Windows 7, Vista, and XP optimizer offers you a multitude of ways to speed up your computer. Cacheman has been developed with novice, intermediate, and expert users in mind. Immediately after installation, Cacheman examines your computer and automatically tweaks a vast number of cache settings, Registry values, system service options, and PC memory parameters.
But this is only the start. Cacheman then continues to work quietly in the background, in order to speed up your computer even more by managing computer memory (RAM), program processes and system services. Cacheman makes sure that the active application gets the maximum possible processing power and available system memory. Cacheman also includes a special optimization for computer games, to prevent slow downs, lag, and stuttering caused by system tools like anti-virus programs.
Fix slow downs, lag, and stuttering in computer games
Cacheman can fix slow downs, lag, and stuttering in computer games including World of Warcraft (WOW) and Star Wars – The old Republic (SWTOR). Cacheman will give more CPU power and make more memory (RAM) available to the game. Slow downs, lag, and stuttering in computer games is often caused by background process activity. For example, a background Virus-Scan performed by an Anti-Virus program can significantly slow down the computer.
Cacheman will dynamically regulate the priority of background processes (Anti-Virus programs, system services, Windows-Update installations) if they take too much CPU processing power. The front running application (in this case the computer game) will get a significant boost. Cacheman will also ensure that applications leaking (wasting) computer memory will not take away resources from the game. The dynamic priority feature is already pre-configured and works from the start.
The first Windows performance optimization software ever!
The initial internet incarnation of Cacheman was introduced in early 1997 as the first Windows optimization application ever released. 15 years and millions of downloads later, Cacheman's 2012 edition is available as Version 7.50, fully supporting Windows XP/Vista and especially designed to speed up a Windows 7 computer. In its rich history Cacheman has been praised by almost every computer magazine world-wide.
Even Microsoft recommended Cacheman 5.11: "Cacheman enables you to tweak the cache settings for your hard drive, CD-ROM drive, desktop icons and file and folder names in much more detail. You can pick a typical profile, use the wizard or just experiment." Read the History of Cacheman for more details, but don't forget to download first!
Installation
1. Unpack rar archive
2. Run installer Outertech Cacheman v7.50.exe
3. Enjoy.
CCProxy 7.2 Incl KeyMaker
| Name: | CCProxy 7.2 Incl KeyMaker |
Description:
CCProxy 7.2 Incl KeyMaker | 1,44Mb
Quote:
| Proxy Server CCProxy is easy-to-use and powerful Internet connection sharing software. CCProxy can support broadband, DSL, dial-up, optical fiber, satellite, ISDN and DDN connections, it helps you build your own proxy server and share Internet access within the LAN efficiently and easily. CC Proxy Server can act as an HTTP, mail, FTP, SOCKS, news and telnet proxy server. It features powerful account management functions, including Internet access control, bandwidth control, Internet web filtering, content filtering and time control. It also provides web caching, online access monitoring, access logging and bandwidth usage statistics functions. CC Proxy is compatible with Win98, WinME, WinNT, Win2000, WinXP, Win2003 and Vista. The first version of Proxy Server CCProxy was developed in June 2000. It was initially designed to modem sharing within a LAN. Proxy Server CCProxy has now been expanded to support Internet connections of many other types, such as DSL sharing, cable modem sharing, wireless sharing, satellite sharing, parent proxy server connection sharing, and more. If there is a computer within a LAN that can access the Internet, all the other computers within the LAN can access the Internet via this proxy server software. This could make great savings for your business in terms of hardware and Internet connection fees. CCProxy can act as web proxy software, which enables you to browse web pages, download files and send and receive e-mails via web browsers such as IE, Firefox, Netscape and etc. The web caching function can increase the Internet surfing speed. CCProxy provides powerful management functions including several ways to control the Internet access on the LAN. They are IP address, IP range, MAC address, User Name/Password and group. It can also merge with Active Directory. The web filtering and content filtering function can restrict clients' access to particular sites. It will help you to ensure that employees concentrate on their work or that children are unable to visit unsuitable sites. The time schedule function is used to control the users' online time. Different proxy services can be allocated to different users. For example, some of them could be restricted to browsing web pages and others to sending and receiving e-mails. CCProxy can allocate proxy client bandwidth as appropriate. That is to say, it can be used to control the users' Internet surfing speed and balance the bandwidth to avoid the network traffic jams that can be caused by users who download big files or watch online media. Access logging and online access monitoring will help you record the clients' Internet access activities. Proxy Server CCProxy Main Features Modem, Cable Modem, ISDN, ADSL, Satellite, DDN and so on are supported(more). HTTP, FTP, Gopher, SOCKS4/5, Telnet, Secure (HTTPS), News (NNTP), RTSP and MMS proxy are supported. Port Mapping is supported. Web cache can enhance browsing speed. The size and refresh time of the cache can be easily changed. Bandwidth control flexibly manages the traffic usage of clients. Time schedule can easily control the clients' on-line time(access time control). Web filter can ban the specified web sites or content, It can also name specific web sites for browsing. URL filtering prevents users from downloading files with designated extensions via IE. There are seven types of account authentication: IP address, IP range, MAC address, User Name/Password, IP + User Name/Password, MAC + User Name/Password and IP + MAC. Parent proxy function enables CCProxy to access the Internet via another proxy. Dial-On-Demand, remote dial up and auto disconnect are supported. Access Logging can keep a full record of the Internet access log. It enables IE and Netscape to access the Internet through HTTP/Secure/FTP (Web)/Gopher. SOCKS5 proxy support allows use of ICQ, MSN Messenger, Yahoo Messenger, CuteFTP, CuteFTP Pro and WS-FTP. Mail proxy supports Outlook, Eudora etc. Supports NetTerm accessing the Internet via Telnet proxy. Supports Outlook connecting to the News server via News proxy. Support SOCKS5 and web authentication. Support for Real Player RTSP proxy and Media Player MMS proxy. Built-in DNS can resolve domain names. Win98/WinMe/WinNT/Win2000/WinXP/Win2003/Vista compatible. Bandwidth usage statistics. Installation Unpack, install, Use KeyMaker to Generate Key and Register Enjoy |



I Check it with McAfee VirusScan Enterprise , it Is clean.
Iconico Data Extractor 3.3 Incl Crack
| Name: | Iconico Data Extractor 3.3 Incl Crack |
Description:
Iconico Data Extractor 3.3 Incl Crack | 1,22MB
Quote:
| Do you have a group of files that contains important data that you can't get to? Using Data Extractor you can simply extract any information from any files on your computer or from html web pages. The Data Extractor allows website screen scraping to simply extract email addresses or URLs, or extract your own information using advanced techniques. Features of the powerful web and file screen scraper: Easily extract Email addresses or URLS from text files or the web Extract as you surf pages using Internet Explorer Automatically follow links to extract from entire domains Extract whatever you want from webpages with our NEW powerful javascript enabled rules Search multiple files, URLs and directories Drag and drop files for extraction Export results directly to Microsoft Excel Use fuzzy matching to find information when you're unsure of exact data Specify wildcards or use advanced regular expressions to match any pattern Copy, Save and Print at the touch of a button Use the feature-limited trial version for an unlimited time Data Extractor runs on all Windows systems: 95/98/NT/2000/Me/XP, after downloading unzip the file and double click the DataExtractor.exe file to install. Installation ================ Unpack, install (Donot Run), Copy cracked file(s) over original(s) Enjoy |
RemotelyAnywhere 10.0.1086 (Server and Workstation) Incl Serial Key
| Name: | RemotelyAnywhere 10.0.1086 (Server and Workstation) Incl Serial Key |
Description:
RemotelyAnywhere 10.0.1086 (Server and Workstation) Incl Serial Key | 22,0MB
Quote:
| Fast, secure system administration FROM ANYWHERE. RemotelyAnywhere offers industry leading security and performance for remote administration. Join the thousands of companies that trust RemotelyAnywhere for ensuring total access to the systems they manage. Drag and Drop File Transfer Remote Sound IPv6 Support Windows Server 2008 Compatible Mini Meeting Disk Mapping 64-bit Compatible System Dashboard Easy Enterprise Deployment SSH & FTP PDA Remote Control Access via Any Web browser Workstation Edition Create a secure access infrastructure for remote support and administration. Server Edition Gain total accessibility to your servers for rapid analysis and administration. more info @http://www.remotelyanywhere.com/ Installation ---------------- Unpack, install, Use Key to Register Enjoy |
Ram Boost Master 6.1.0.8146 + Serial Key

Ram Boost Master 6.1.0.8146 + Serial Key || File Size : 1.90 MB.
It optimizes your cache to act as a ram booster, boosts up your computer speed, frees up RAM memory and makes your computer faster and stable. It will compress physical memory and will recover used memory from Windows and other applications. It is an easy and powerful tool for both beginners and experts.
RAM Boost Master boosts the physical memory available to Windows 2000/2K/XP. You don't need to reboot your computer anymore. Our application integrates both process and startup manager. It has an easy to use interface that will display information about free and used physical memory, free and used page file, CPU usage and clipboard content. You can use the schedule feature to optimize the memory when you are away from the computer.
Installation
1. Unpack rar archive
2. Run installer Ram Boost Master 6.1.0.8146 .exe
3. Enjoy.
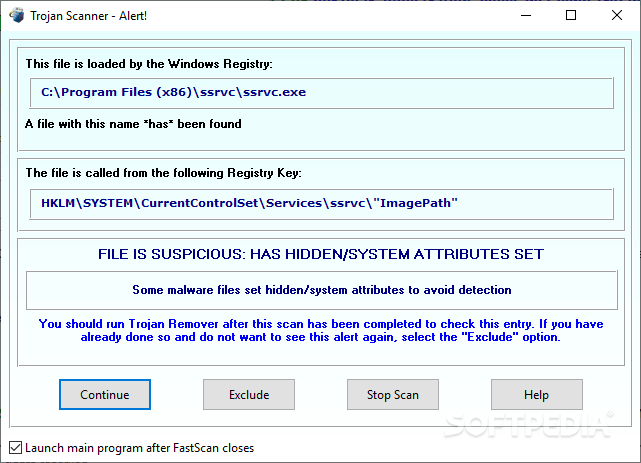
TORJAN REMOVER 6.8.2+ Keys
Detects and automatically removes malware without the need to use SAFE mode.
Trojan Remover is designed to automatically remove malware (trojans, worms, adware, spyware, etc.) from a PC when standard anti-virus software has either failed to detect the malware or is unable to effectively eliminate it.
Trojan Remover aids in the removal of Malware - Trojan Horses, Worms, Adware, Spyware - when standard anti-virus software either fails to detect them or fails to effectively eliminate them. Standard antivirus programs are good at detecting this Malware, but not always so good at effectively removing it.
Trojan Remover is designed specifically to disable/remove Malware without the user having to manually edit system files or the Registry. The program also removes the additional system modifications some Malware carries out which are ignored by standard antivirus and trojan scanners.
What Trojan Remover Does
Trojan Remover examines all the system files, the Windows Registry and the programs and files loaded at boot time. The majority of malicious programs (once triggered) load this way.
Trojan Remover scans ALL the files loaded at boot time for Adware, Spyware, Remote Access Trojans, Internet Worms and other malware. Trojan Remover also checks to see if Windows loads Services which are hidden by Rootkit techniques and warns you if it finds any.
For each identified Trojan Horse, Worm, or other malware, Trojan Remover pops up an alert screen which shows the file location and name; it offers to remove the program's reference from the system files and allows you to rename the file to stop its activation.
Most modern Malware programs are memory-resident, which makes their de-activation more difficult. How many times have you been told to start your computer in 'Safe' mode, or even worse, in DOS? Trojan Remover does all this for you. When it finds Malware that is memory-resident, Trojan Remover automatically re-starts (on request) your system and completely DISABLES the Malware before Windows restarts.
Trojan Remover writes a detailed logfile every time it performs a scan. This logfile contains information on which programs load at boot-time, and what (if any) actions Trojan Remover carried out. The logfile can be viewed and printed using Notepad.
The FastScan component of Trojan Remover is set to automatically scan for Malware every time you start your PC (you can disable this if you wish). You can also run the FastScan manually any time you wish (START | Programs | Trojan Remover | FastScan). This FastScan checks all program-loading points - it is a quick and effective check for actively-loading malicious programs.
You can scan the whole drive, or any directories on the drive, by selecting Scan a Drive/Directory from the main Trojan Remover menu. You can scan individual files and directories from within Windows Explorer.
Trojan Remover incorporates an integral Updater allowing for quick and easy Database updates. You can use the Windows Task Scheduler to schedule automatic updates.
Note: Trojan Remover will not work on 64 bits operating systems.
Download
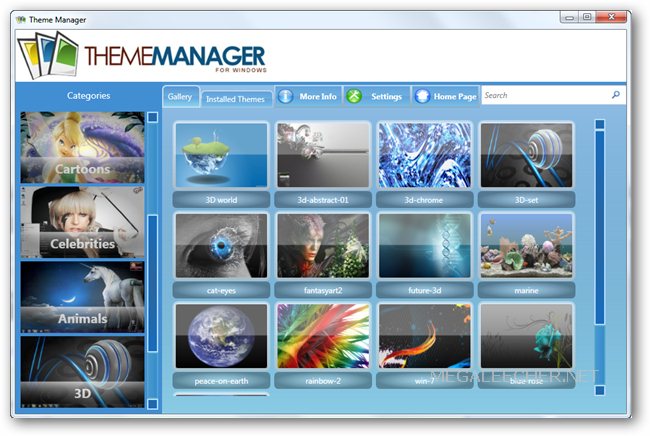
Window 7 Theme Manager-Easy Solution To Browse And Install Unofficial And Third Party Themes
Theme Manager - a free utility for Windows 7 allows users to browse and install hundreds of unofficial themes from a single easy to use interface. Neatly divided into 15 different categories - TV Series, Landscape, Celebrities, Animals, Movies, 3D, Cars, Space, Motorcycle, Cartoons, Games, Anime, Computers, Sport, and Abstract users simply need to click on a theme's icon to instantly download and apply the theme.
Managing installed themes is also very simple, just switch to "Installed Themes" tab and you have all the options to manage already installed themes including uninstallation, New themes are automatically added to the catalog.
Windows 7 Theme Manager
Download Windows 7 Theme Manager :
Subscribe to:
Comments (Atom)